Gli attacchi Ransomware possono colpire anche Linux?
Nelle ultime settimane si è sentito molto parlare di un attacco Ransomware verso la piattaforma Microsoft Windows, così mi son chiesto se un tale attacco possa esser replicato anche sui PC Linux.
Per prima cosa, col supporto di Wikipedia ecco la definizione di Ransomware:
“Un ransomware è un tipo di malware che limita l’accesso del dispositivo che infetta, richiedendo un riscatto (ransom in Inglese) da pagare per rimuovere la limitazione. Ad esempio alcune forme di ransomware bloccano il sistema e intimano l’utente a pagare per sbloccare il sistema, altri invece cifrano i file dell’utente chiedendo di pagare per riportare i file cifrati in chiaro. Inizialmente diffusi in Russia, gli attacchi con ransomware sono ora perpetrati in tutto il mondo.“
Detto questo, ovviamente non sono stato l’unico a chiedersi una cosa simile, infatti su Reddit è iniziata una bella discussione al riguardo (ovviamente in Inglese), di cui vorrei proporvi un estratto esaustivo (ad oggi, col passare del tempo nuove risposte si aggiungono alla discussione).
Il topic inizia con la domanda di un utente, Rytuklis, che esordisce così:
“I am sure you guys heard the news about that huge hacker attack that locks peoples personal fines and demands ransom. Is Linux secure enough to protect against such attacks? I thought I was safe on Windows in Lithuania where such attacks are very rare but saw this hack also hit Lithuania pretty hard too, so it makes me contemplate Linux again.“
Ed ecco le risposte che desidero riportarvi:
Chrisoboe: “These attacks only worked because people didn’t update their Windows, or used an out of support version. Every operating system is insecure if you don’t update it or if you use out-of-support versions. Linux distros usually provide security updates way faster than Microsoft, but that doesn’t matter much when users decide not to do updates. ”
ArcadeStallman: “Linux and Windows are both secure enough if you exercise caution and keep your system updated. It’s easier to keep Linux updated, though, since you can update with one or two commands and not have to restart immediately. This particular attack won’t affect Linux AFAIK, but attacks targeted at Linux systems do happen occasionally.”
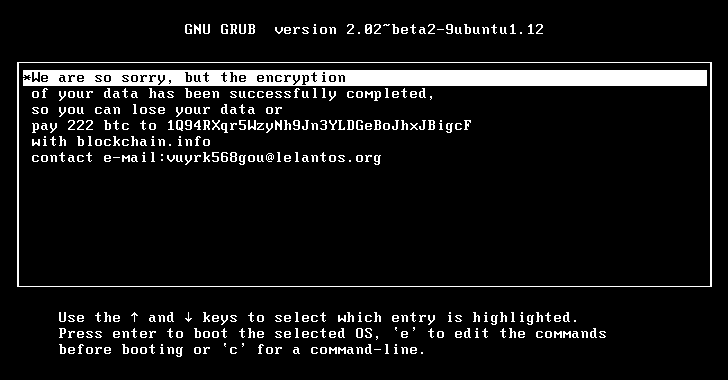
Tscs37: “Short answer: No.
Long answer: No, but not many people find it profitable or lucrative to make Linux-based ransomware.
No software is 100 percent bulletproof. Linux may be a bit better but it’s hard to estimate by how much in hard numbers. CVE’s are a good start but don’t cover possible exploits or overall security at all.”
Destiny_functional: “More secure than Windows. Windows has a 20 year history of leaving its users vulnerable on the internet. Frequent major vulnerabilities too. We had MSBlast which easily could have been ransomware too if it had been invented / famous then. MSBlast basically made any new Windows 2000 or XP version that you would connect directly (i.e. not behind a router) to the internet useless within a minute. I don’t see that much has changed. Seeing which Windows version patches were released for the last couple of days you see how extremely old (XP era) vulnerabilities carry over from version to version seemingly. That’s Microsoft for you and has always been. Is Linux secure enough? Security always can be (and needs to be) improved. Anyway, if you have backups you have nothing to fear.”
Perillamint: “MO, limit scope to this issue, Linux is better then Windows. At least, nobody (unless they’re crazy enough and smart enough to patch kernel) runs SAMBA on Ring 0 on Linux unlike Microsoft did (and allowed RCE to Ring 0 🙁 ).”
Audioen: “Security needs to be designed in, and then the implementation itself must be correct. Linux shares the history with Windows in that its security resembles that of an egg: a hard exterior meant to keep intruders out, but once through the shell, you meet a soft interior that offers little resistance. Many Windows vulnerabilities require a vector that allows code execution, then the payload facilitated by that tends to use any of the numerous unpatched security holes to do whatever it wants on the system. Additionally, recovery to uncompromised state requires treating the machine to a complete reinstall. Categorically, Linux is very much in the same boat in that services running on the system can serve as the vector to inject a payload, which can then burrow into the system so deep that the only way you can be sure you have got rid of it is by reinstalling the OS. (In fact, some proof-of-concept virus-type programs are so advanced that they can in infect e.g. certain hard disk firmwares, in which case reinstalling does not necessarily help.). However, many vectors used on Windows are not working well on Linux: e.g. people don’t usually download random executables from the web and run them, people don’t blindly execute attachments they received by email, etc. Still, the situation is not ideal and requires constant vigilance, and there are tools you’re supposed to install by sudoing a Bash script you download from GitHub etc. At the current state of security, allowing users to learn to do things like that invites disaster. A hardened operating system would be basically impossible to destroy by any user action, and could be brought back to a known-safe state at any point the user wants. It would probably substantially remind one of iOS, Android, or ChromeOS in that the user (and by extension any program the user can run) always has less than full control of the machine, and even then security can fail due to implementation errors.”
Ironfish: “Linux, just like Windows, is as secure as you make it. I’ve seen plenty of Linux boxes get rooted over the years so it’s not a magic bullet to just switch to another OS.”
Turin231: “Both OSs can be secure enough if you follow good practices. Basically keep everything updated. Linux is just more secure because vulnerabilities are patched faster (easier to find and cannot be hidden by the developer), CVE practices tend to be more complete, and there is usually no data-mining software that can be potentially exploited by third parties. But more secure does not mean fully secure. No system can provide this.”.
———————–
Sostanzialmente, viene in prima istanza sottolineata la latenza eccessiva, da parte di Microsoft, nell’identificare e chiudere qualsiasi “buco” presente nel proprio sistema operativo, il che permette ai malintenzionati di sviluppare e diffondere virus e software (in generale) che possano comprometter i pc in questione.
In secondo luogo, la natura di Linux, ovvero open source, permette a chiunque di individuare, segnalare e chiudere le falle (nessuno è perfetto!), ed in generale la reattività della community del Pinguino permette di anticipare eventuali attacchi. Attenzione però, nessuno dice che non esistano Ransomware per sistemi Linux, come dimostra questo articolo di Tom’s Hardware dal titolo “Non serve pagare per il ransomware su Linux”.
Ovviamente occorre anche tenere conto del tasso di adozione di Linux, che ha il monopolio lato Server, ma ha una percentuale di adozione bassissima lato PC Desktop. Tale fattore ovviamente sposta le attenzioni dei soggetti con interessi malevoli verso Windows, che lato Desktop la fa da padrona.
Ovviamente non bisogna trascurare l’utilizzo dell’Utente (Utonto alle volte) del proprio PC, spesso la disinformazione informatica porta alcuni utenti a cliccare su link fasulli come il seguente:

Quindi, in generale, è vero che un Sistema operativo aggiornato è “più sicuro” di altri, ma le azioni dell’utente potrebbero aprire le porte del proprio hard disk a chiunque, con un semplice Click!